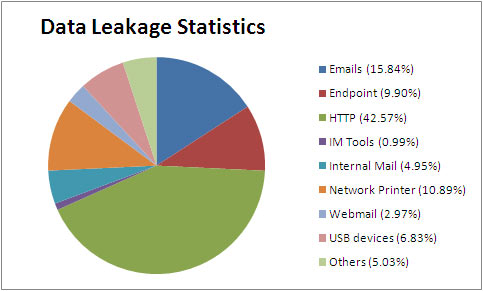
Data leakage involves the deliberate or accidental release of sensitive data pertaining to finances, customers, intellectual property and other confidential information. Sensitive data includes private and personally identifiable information that can be used to uniquely identify, locate or contact a single individual. Data Leakage Prevention solution is a system that is designed to detect potential data breach / data ex-filtration transmissions and prevent them by monitoring, detecting & blocking sensitive data from getting transported or from restricting viewing by unauthorized persons or entities. Data leak prevention (DLP) is a suite of technologies aimed at stemming the loss of sensitive information that occurs in enterprises across the globe. By focusing on the location, classification and monitoring of information at rest, in use and in motion, this solution can go far in helping an enterprise get a handle on what information it has, and in stopping the numerous leaks of information that occur each day. DLP is not a plug-and-play solution. The successful implementation of this technology requires significant preparation and diligent ongoing maintenance. Enterprises seeking to integrate and implement DLP should be prepared for a significant effort that, if done correctly, can greatly reduce risk to the organization. Those implementing the solution must take a strategic approach that addresses risks, impacts and mitigation steps, along with appropriate governance and assurance measures.
Business cases for DLP
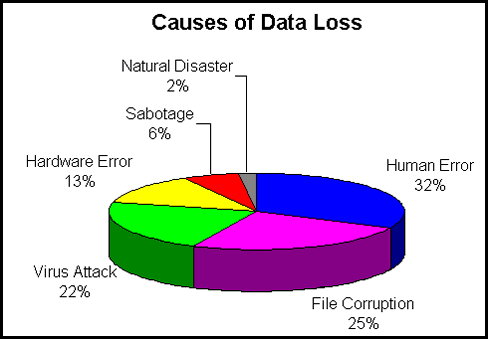
- 1. A current or former employee absconding with millions of dollars in intellectual property via unsecured network
- 2. A consultant deliberately transmitting and releasing sensitive data about a well-known figure who happens to be a client or patient.
- 3. Information about an upcoming product being leaked via online social media outlets (Twitter, Facebook, etc).
- 4. The accidental leaking of sensitive information, including identification and bank account data for dozens or hundreds of employees.
- 5. Forwarding confidential data such as intellectual property and trade secrets to the wrong e-mail recipient.
- 6. Source code files for a company’s product being sent to a competitor.
- 7. Unsecured data being intercepted by malicious parties while being transmitted along an unsecured network.
GIT can help organizations complete all the necessary steps to develop, implement and operate a successful data leakage prevention program including;
- 1. Define a formal data security policy
- 2. Develop measurements to manage & track
- 3. Select and deploy technology that is focused on protecting and detecting mishandled data
- 4. Create process and procedure, as well as automate compliance and protection
- 1Disaster Recovery Solutions
- 2Business Continuity Solutions
- 3Data Migration & Cleansing
- 4Data Leakage Prevention
- 5Storage Designing
- 6Managed IT Services
- 7Service Desk
- 8Server Performance Monitoring
- 9Application Performance Monitoring
- 10Network Performance Monitoring
- 11Infrastructure As A Service
- 12Remote Infra Management
